The user selects an S/Key password K and a maximum sequence number N. The system supplies a seed k. These are hashed together (specifically: k and K are concatenated, run through the MD4 cryptographic hash function, and shortened to 64 bits by xoring the two 64-bit halves) to form h. The system then computes the following sequence of passwords p0, ..., pN-1:
Note that pi = fN-i(h), or pi = f(pi-1), for 0 ≤ i < N.
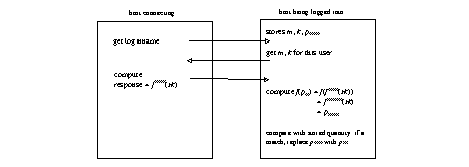
The system stores the current count m, the seed k, and the last validated password pm-1 in a file called skeykeys.
In the following algorithm, localhost is the host which the user is logged in to and remotehost is the host that the user is trying to log in to from localhost. The S/Key mechanism is to be used.
The picture below summarizes this exchange:
